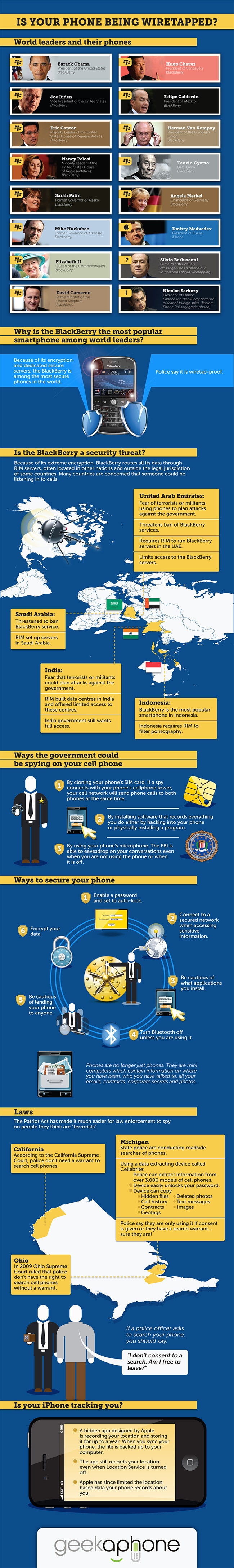
Ever since the first mobile phone surfaced on the market, celebrities around the world have been seen on their phones texting while driving, screaming on their phones while in line at the grocery store, and many other unexpected places. You can probably think of quite a few more examples. What we haven’t seen until recently is that we have always thought ourselves to be safe when we are on the phone with our friends and loved ones.
However, for celebrities, in the year of 2011 that is no longer something to count on. With the scandal revealed about a year ago, and again just a few weeks ago about an English newspaper who wiretapped celebrity’s cellphones and listened to them talk and listened to their voicemails, it seems we’ve entered a completely different technology landscape. It’s now a world where we can no longer know what is being done behind our backs.
It’s been said that the iPhone collects data about our location and so forth and stores it on a server somewhere. I am not very read up about the topic and should probably not make any accusations, but by the sound of it, that’s something that could actually be true. It would mean a huge advantage for Apple if they could get that information about us and put it on an extensive list and use it for research to help them grow their business.
The people at geekaphone have compiled a boatload of information about this issue, and in surface detail explained just what is being done behind our backs on the very cell phone that we could be holding in our hands right now. The question is really, what you are prepared to do about it? Are you scared, and do you want to switch out your phone for another, safer one? Will you give up your cell phone usage entirely and go back to smoke signals instead? Not that that will solve anything, but maybe it’s worth a try. I guess the only thing left to ask is really, from now on will you think twice before you say certain things on the phone since you could be wiretapped at this very moment?
Click Image To Enlarge
COMMENTS